01.The growing importance of records
As business becomes more reliant on IT, business processes digitization is accelerating. More than ever, keeping records of data access is vital for monitoring and preventing fraud and data theft.

As business becomes more reliant on IT, business processes digitization is accelerating. More than ever, keeping records of data access is vital for monitoring and preventing fraud and data theft.

ALog offers unique data analysis technology and unparalleled ease of use.
Many security-conscious companies continue to choose Amiya for their data security needs.
Reason #1
We extract vast amounts of data access records from complex system data, compiling records into an easy-to-read access log using unique log analysis and conversion technology.
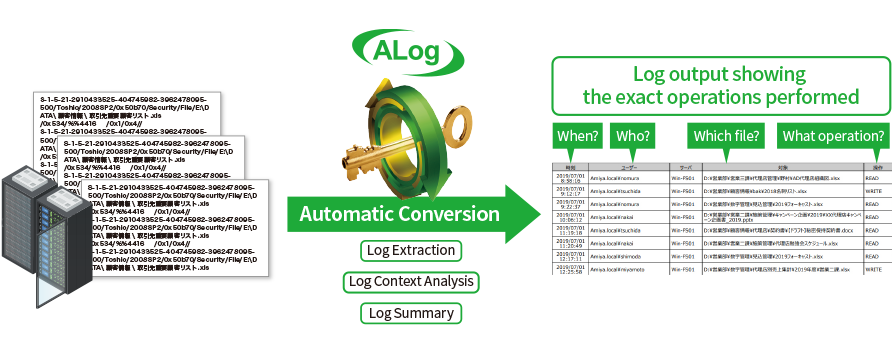
Reason #2
All search, report and management functions are accessible through a central, intuitive
interface.
We offer a search engine specialized in high-speed search of time-series data.
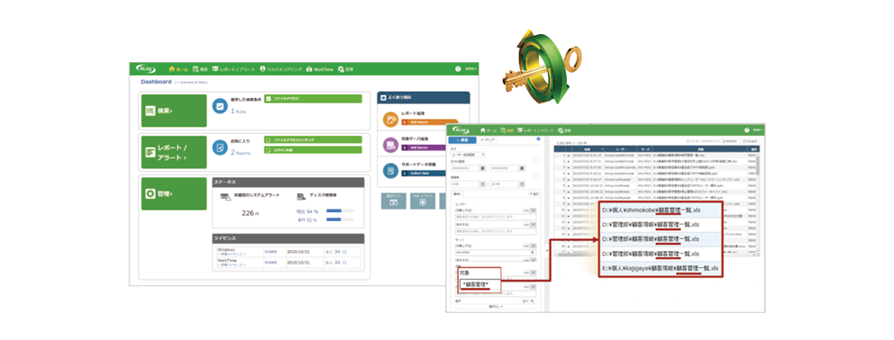
Reason #3
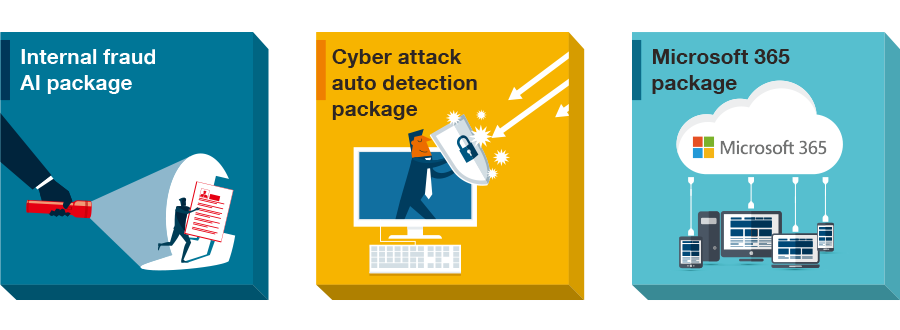
Define content to monitor in advance for automated reports and alerts.
We offer cyber-attack detection packages and other predefined templates for users who prefer a simpler set up.
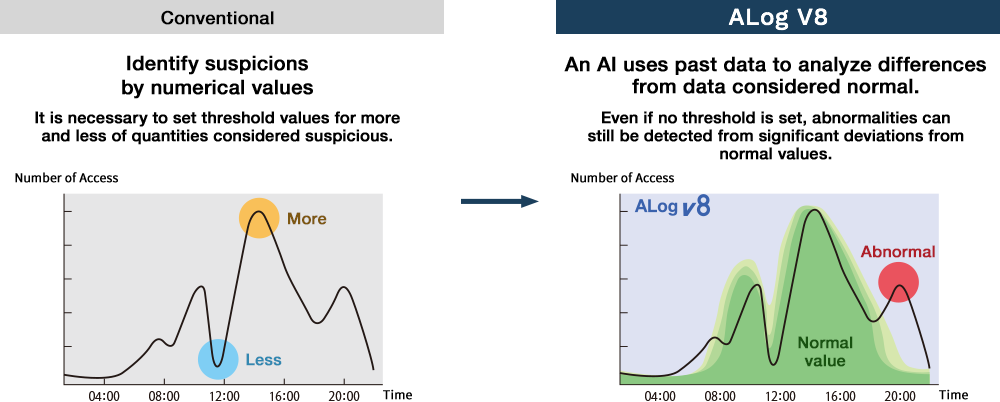
The ALog Series plays an active role as a record data bank.
More recently, our ALog Series as data sets for AI and big data (pre-processing to organize data), as well as a data analysis platforms.


Since launch, ALog has been adopted by a wide variety of major corporate customers across a broad range of industries. Today, we boast the title of No.1 Server Access Log package in the market.

Source: https://mic-r.co.jp/mr/02620/ Deloitte Tohmatsu MIC Research Institute Co., Ltd.
Current Status and Future Prospects of the Internal Threat Countermeasure Solution Market 2022" Published in January 2023





















Logs are important data that can be used to solve a variety of corporate problems. This book introduces how logs can be used by those new to log management.

Focusing on the fact that all cyber attacks go through Active Directory, we will focus on Active Directory as a countermeasure against internal fraud, and explain AD countermeasures and AD log management.

We explain three typical oversights that can result from "unnoticed logs" and the operational issues that lie behind them.

It is a collection of log management know-how that can be used by both beginners and experts.

From the basics of [why not notice cyber attacks] to [creating a concrete mechanism for automatic detection]. Introducing efficient cyber security measures from the perspective of log management.

Introducing a method to automatically manage "security measures for cloud services" using Microsoft 365 as an example.
A telework environment that is a hotbed for cyber attacks. Where is the threat lurking? Introducing the points of countermeasures while unraveling the attack method.

Information leakage incidents with a loss of over 400 million yen can occur on a daily basis! Based on damage cases mainly due to internal fraud, we analyze information leakage routes and introduce efficient monitoring points.

Introducing ALog

Introducing Resource Athlete
