01.Overview
ALog EVA expands the scope of the ALog series dramatically. A new integrated data management tool offering ease of use and flexibility that sets it apart from the traditional, hard-to-understand log products.
ALog EVA expands the scope of the ALog series dramatically. A new integrated data management tool offering ease of use and flexibility that sets it apart from the traditional, hard-to-understand log products.

Point 1
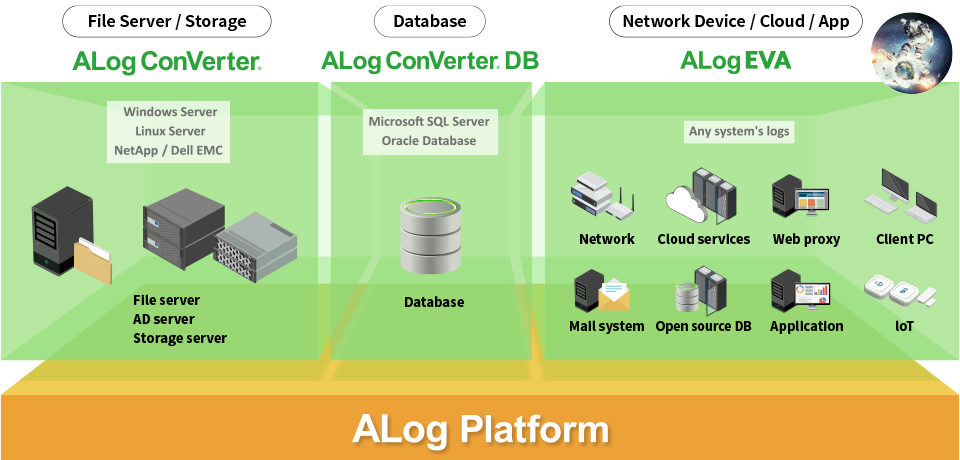
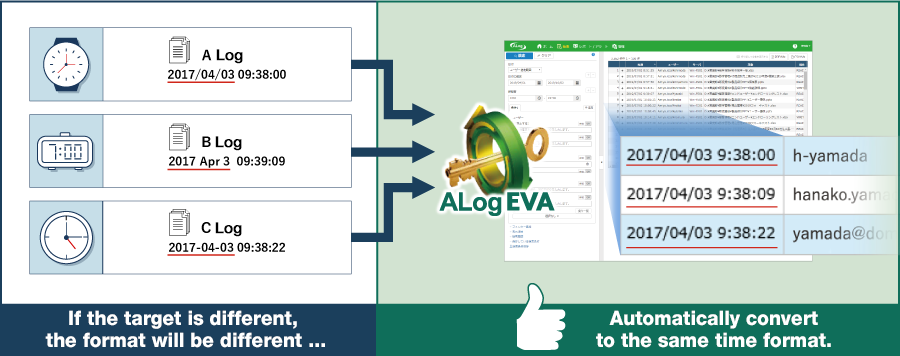
The most challenging part of log management is changing data collected from various sources into a uniform format. EVA recognizes time format automatically and converts data to a common format.Simple, centralized data management.
Point 2
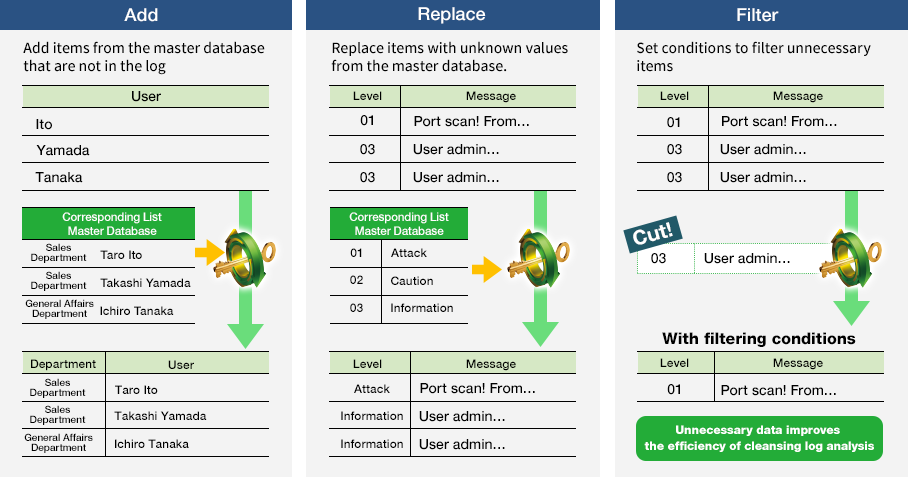
EVA offers integration using information from a master database without complicated syntax, even if information for a piece of data is lacking.
Point 3
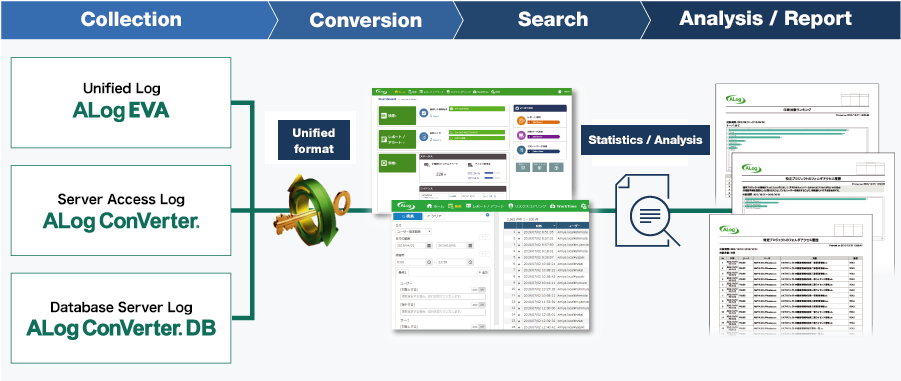
The captured logs are integrated and managed using the common interface throughout the ALog series.
With an all-in-one pack, users can manage an entire chain of data without having to install extra options.
Point 4
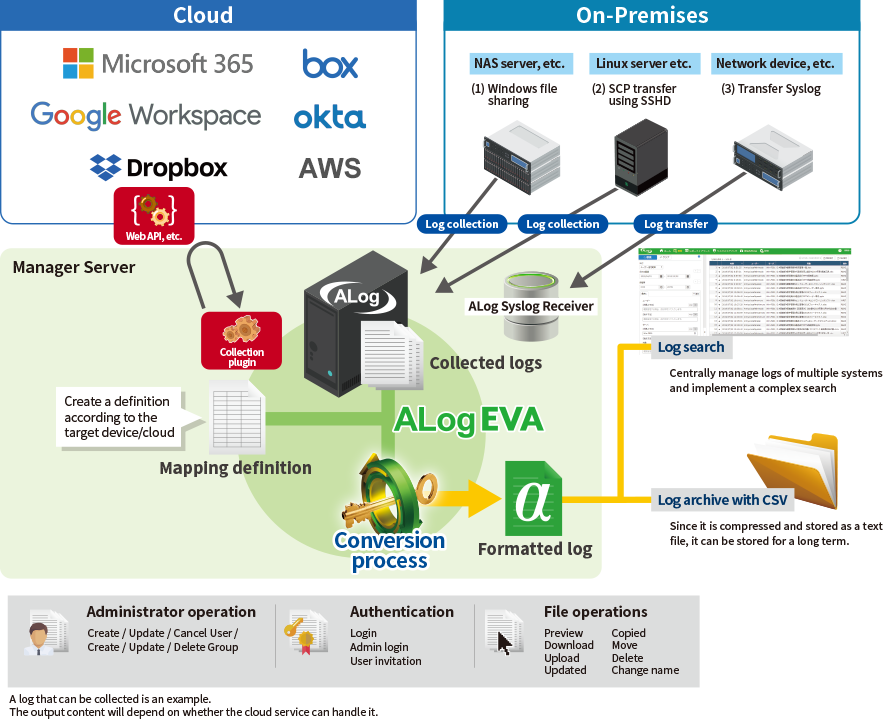
EVA aggregates logs for cloud applications such as Microsoft 365, box, and more.
* As of the end of June 2022, random order.
| Location |
On-premises environment
|
|---|---|
| Supported OS |
Windows Server 2016 / 2019 / 2022
|
| CPU | 2.7GHz with 8 cores or more recommended |
| Memory | 32GB or more recommended) |
| HDD |
500GB or greater available disk space.
|
| Required Software |
.NET Framework 4.8 or later version Any of the following Web browsers: Firefox 68 or later Google Chrome 76 or later Microsoft Edge |
*A manager server license is not required.
The following types of files cannot be collected.
In addition, the following types of logs cannot be collected.
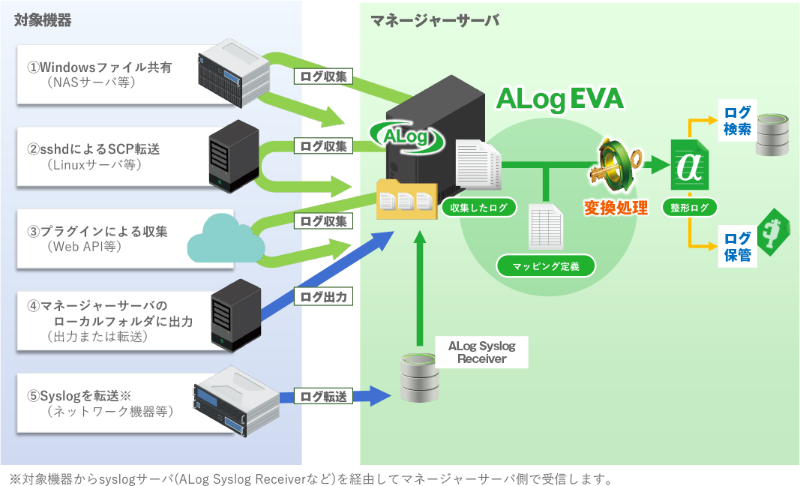
ALog EVA is an integrated logging product that collects log file types not supported by other ALog Series.
EVA collects logs of various types, allowing businesses to monitor for external attacks going through their network, rank employees by work speed, and calculate employee overtime to implement work-style reform. In this way and others, EVA helps businesses adopt a wide range of security measures.
EVA collects event logs, Syslogs, delimited text (CSV, etc.), and plain text logs.
Log file collection supports uncompressed files, ZIP files (Deflata 32), as well as gz and bz2 compressed files.
The text files must use a character code supported by the .NET Framework, such as Shift-JIS, UTF8, or UTF16.
See a list of actual ALog EVA applications on our corporate website.
https://www.amiya.co.jp/english/solutions/alog_eva/
We can create templates based on your sample data for any applications that have not had EVA implementations.
Yes.
We have prepared a GUI for creating and editing templates.
The ALog Syslog Receiver is a free application for customers who use ALog EVA.
The application receives Syslogs sent from each device and outputs the content as a file.
Select the size range that matches the total size of logs to be collected by ALog EVA in one day.
A license is required according to the size range of total log size, regardless of the number of target machines.

Introducing ALog

Introducing Resource Athlete

It is a collection of log management know-how that can be used by both beginners and experts.

From the basics of [why not notice cyber attacks] to [creating a concrete mechanism for automatic detection]. Introducing efficient cyber security measures from the perspective of log management.

Introducing a method to automatically manage "security measures for cloud services" using Microsoft 365 as an example.
A telework environment that is a hotbed for cyber attacks. Where is the threat lurking? Introducing the points of countermeasures while unraveling the attack method.

Information leakage incidents with a loss of over 400 million yen can occur on a daily basis! Based on damage cases mainly due to internal fraud, we analyze information leakage routes and introduce efficient monitoring points.
